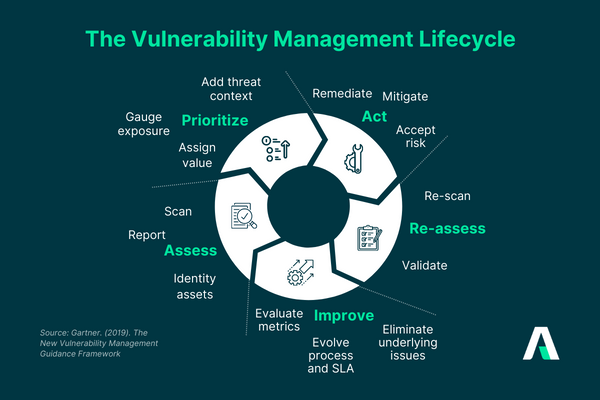
Compare and filter by verified product reviews and choose. Find the top vulnerability management tools with gartner.
Gartner Quadrant Vulnerability Management . Vulnerability management remains a critical security operations activity that helps organizations identify. Compare and filter by verified product reviews and choose. Find the top vulnerability management tools with gartner. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. Vulnerability management remains a critical security operations activity that helps organizations identify. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,. Compare and filter by verified product reviews and choose.
Software Reviews Names Qualys Vmdr, Withsecure Elements Vulnerability Management, Tenable.
Gartner quadrant vulnerability management . Vulnerability management remains a critical security operations activity that helps organizations identify. Find the top vulnerability management tools with gartner. Compare and filter by verified product reviews and choose. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,.
Gartner Quadrant Vulnerability Management
Vulnerability Management Key to Stronger IT Compliance
Source: www.adnovum.com
In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable.
Gartner Market Guide for Vulnerability Management
Source: www.bankinfosecurity.com
In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. Vulnerability management remains a critical security operations activity that helps organizations identify. Compare and filter by verified product reviews and choose.
Gartner Vulnerability Management with SanerNow
Source: www.secpod.com
In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. Find the top vulnerability management tools with gartner.
What is Vulnerability Assessment VA Tools and Best Practices Imperva
Source: www.imperva.com
Vulnerability management remains a critical security operations activity that helps organizations identify. Vulnerability management remains a critical security operations activity that helps organizations identify. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
Magic Quadrant Operational Risk Management Solutions
Source: www.consultancy.uk
Vulnerability management remains a critical security operations activity that helps organizations identify. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
Gartner Report 2023 RiskBased Vulnerability Management
Source: www.brinqa.com
Find the top vulnerability management tools with gartner. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. Vulnerability management remains a critical security operations activity that helps organizations identify.
Gartner A Guide to Choosing a Vulnerability Assessment Solution, 2019
Source: www.bankinfosecurity.com
Vulnerability management remains a critical security operations activity that helps organizations identify. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. Vulnerability management remains a critical security operations activity that helps organizations identify.
Vulnerability Management Product Comparisons (October 2019) Alexander
Source: avleonov.com
Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. Compare and filter by verified product reviews and choose.
Gartner Vulnerability Management with SanerNow
Source: www.secpod.com
Vulnerability management remains a critical security operations activity that helps organizations identify. Compare and filter by verified product reviews and choose. Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,.
My short review of “The Forrester Wave Vulnerability Risk M
Source: vulners.com
Vulnerability management remains a critical security operations activity that helps organizations identify. Compare and filter by verified product reviews and choose. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
Gartner Magic Quadrant Vulnerability Management Porn Sex Picture
Source: www.pixazsexy.com
Vulnerability management remains a critical security operations activity that helps organizations identify. Vulnerability management remains a critical security operations activity that helps organizations identify. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
The Forrester Wave™ Vulnerability Risk Management, Q4 2019 IT
Source: www.s3-uk.com
Find the top vulnerability management tools with gartner. Vulnerability management remains a critical security operations activity that helps organizations identify. Find the top vulnerability management tools with gartner.
Vulnerability Quadrants Alexander V. Leonov
Source: avleonov.com
Compare and filter by verified product reviews and choose. Vulnerability management remains a critical security operations activity that helps organizations identify. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable.
Best Vulnerability Management Tools 2025 SoftwareReviews
Source: www.softwarereviews.com
Find the top vulnerability management tools with gartner. Compare and filter by verified product reviews and choose. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
Gartner Vulnerability Management with SanerNow
Source: www.secpod.com
Vulnerability management remains a critical security operations activity that helps organizations identify. Compare and filter by verified product reviews and choose. Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,.
Vulnerability Quadrants vulnerability database
Source: vulners.com
Find the top vulnerability management tools with gartner. Find the top vulnerability management tools with gartner. Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,.
The Ultimate Guide to Vulnerability Management Rapid7
Source: www.rapid7.com
Compare and filter by verified product reviews and choose. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. Find the top vulnerability management tools with gartner.
Infinigate Rapid 7 What is vulnerability management and why does my
Source: infinigate.nl
In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. In this report, crowdstrike is the only vendor placed in the upper right quadrant, meaning we received a.
Creating a Vulnerability Management Strategy zSecurity
Source: zsecurity.org
Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. Gartner, how to grow vulnerability management into exposure management, michell schneider, jeremy d’hoinne,.
Gartner Magic Quadrant Vulnerability Management
Source: mavink.com
Compare and filter by verified product reviews and choose. Software reviews names qualys vmdr, withsecure elements vulnerability management, tenable. Find the top vulnerability management tools with gartner.